Beware of Airplane WiFi: New Federal Advisory Highlights Security Risks

FRESNO, California – Cody Sarhan, Communications Specialist
Airplane WiFi has become a staple for modern travelers, providing a way to stay connected during flights. However, recent warnings from federal authorities highlight significant security concerns that passengers need to be aware of.
Learn More: Find out how Xobee can safeguard your data from external threats
Federal Advisory: What You Need to Know
A new advisory has been issued warning passengers about the risks associated with using in-flight WiFi. The alert comes after several incidents where cybercriminals exploited airplane WiFi networks to steal personal data from passengers.
The Threat of Fake WiFi Networks
One of the main threats identified is the creation of fake WiFi hotspots by hackers when on a plane or in an airport. These malicious networks are designed to look like legitimate in-flight WiFi, tricking passengers into connecting — sometimes using the airlines’ official names. These same attacks can be found on the ground; in cafes, hotels, conventions, and more.
Once connected, hackers can intercept data transmitted over the network, including personal information, login credentials, and financial details. These types of attacks are known as “rogue access points” or “evil twin” attacks.
Recent Incidents Highlight the Risks
In a recent case, passengers on a transcontinental flight were targeted by a hacker who set up a fake WiFi network named after the airline’s official service. Passengers who connected to this network were redirected to a phishing site that requested their personal information. Many unsuspecting travelers entered their email addresses and passwords, unknowingly giving hackers access to their accounts.
How to Protect Yourself
To safeguard your personal information while using in-flight WiFi, follow these essential tips:
- Verify the Network Name: Always verify the official network name with flight attendants or through the airline’s official communication channels before connecting. Avoid networks with similar but slightly different names.
- Use a VPN: A Virtual Private Network (VPN) encrypts your internet connection, making it much harder for hackers to access your data. Ensure your VPN is active before connecting to any public WiFi, including in-flight networks.
- Avoid Sensitive Transactions: Refrain from conducting sensitive transactions, such as online banking or shopping, while connected to in-flight WiFi. If necessary, use secure payment methods like PayPal instead of entering your credit card information directly.
- Disable Auto-Connect: Prevent your device from automatically connecting to available networks by turning off the auto-connect feature. This reduces the risk of inadvertently connecting to a malicious network.
- Forget Networks After Use: Once you’ve used the in-flight WiFi, make sure to forget the network on your device to prevent it from automatically reconnecting in the future.
What Airlines Are Doing
Airlines are taking steps to enhance the security of their in-flight WiFi services. Many are investing in more secure network infrastructures and providing passengers with detailed instructions on how to safely connect to their services. However, passengers must remain vigilant and proactive in protecting their data.
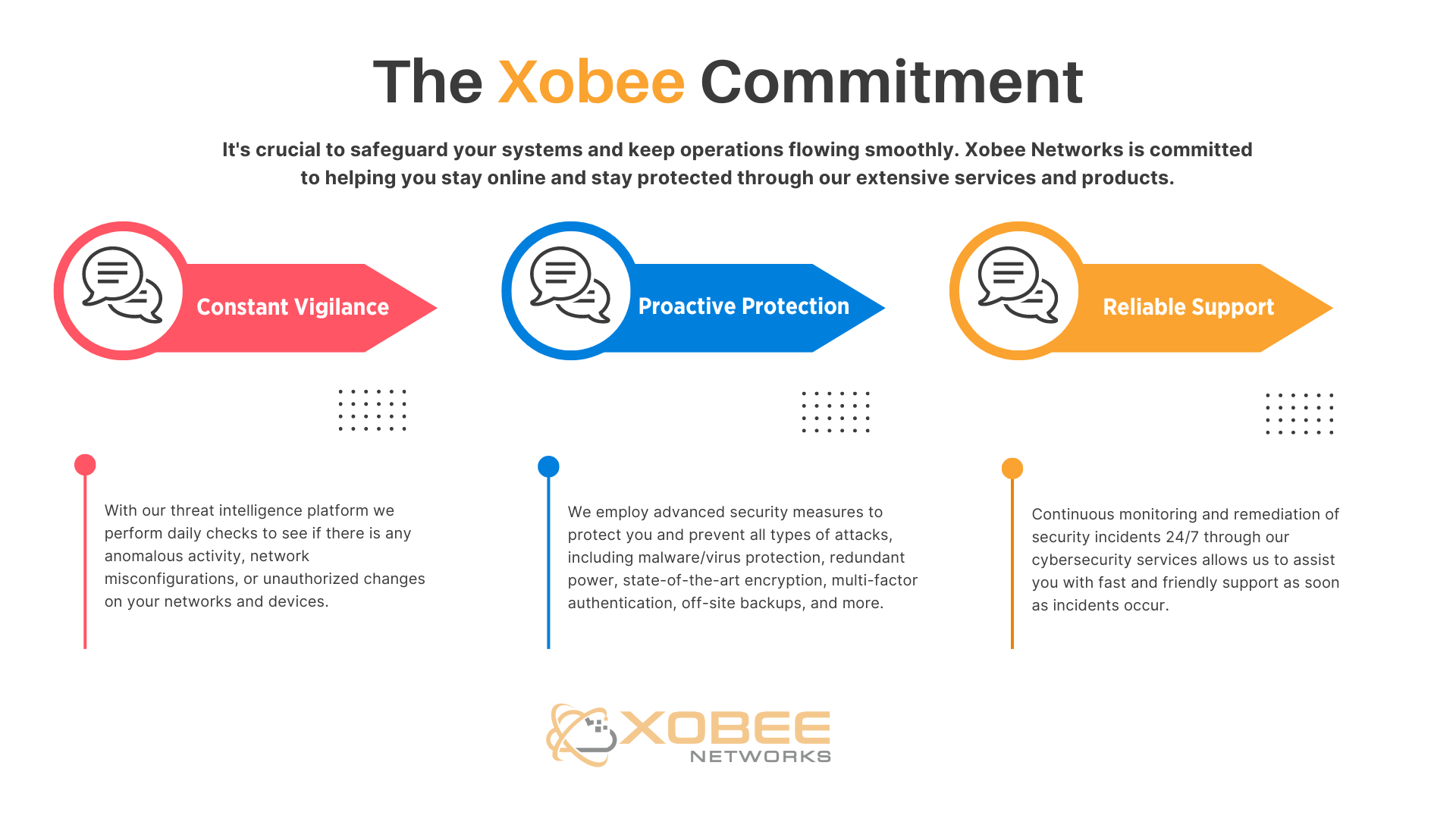
While in-flight WiFi offers convenience, it also presents risks that travelers must consider. By taking a few precautionary steps, you can enjoy the benefits of staying connected while minimizing the dangers posed by cybercriminals.
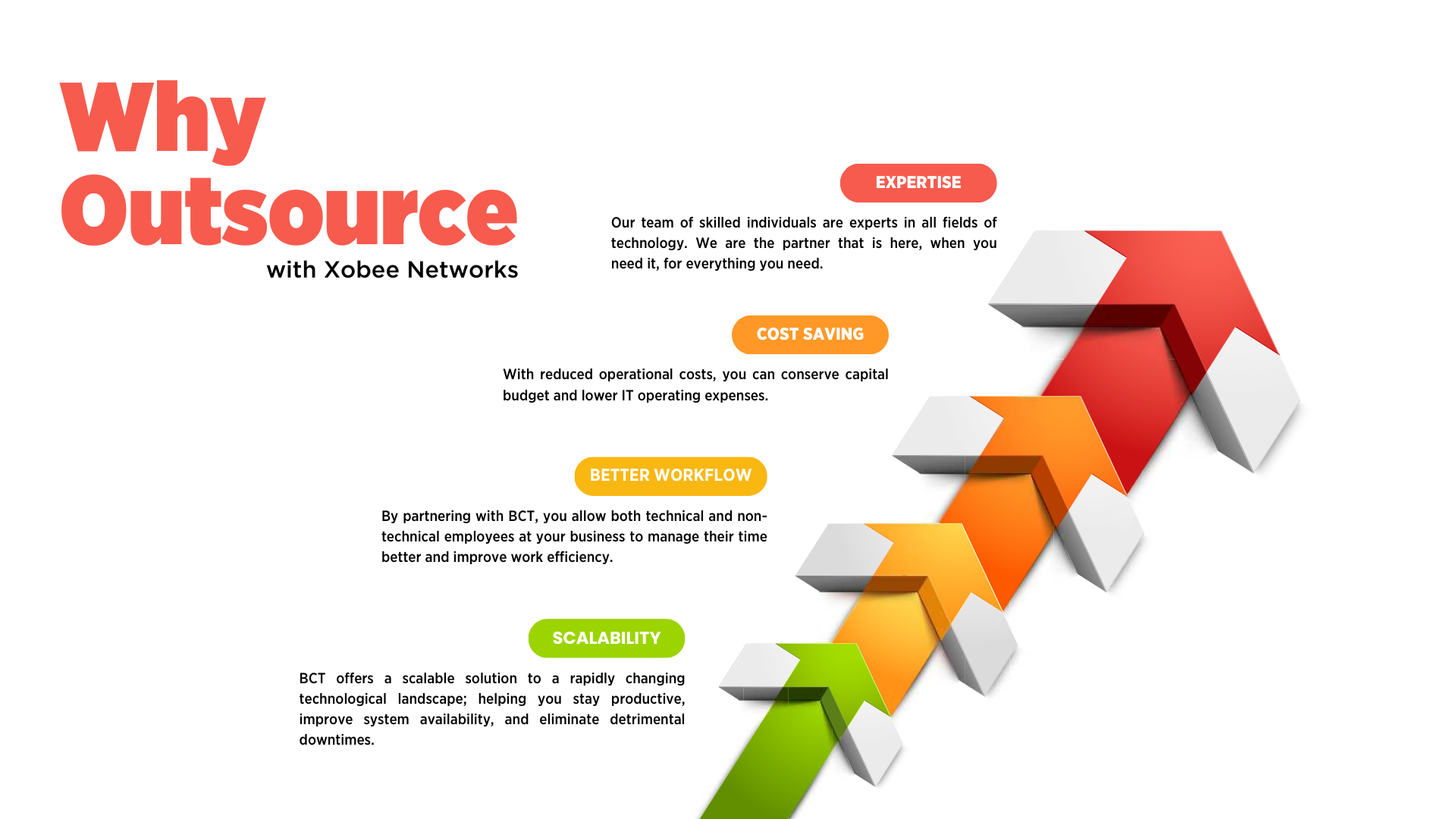
Xobee Networks: Here to Help
For businesses, securing your data and ensuring safe internet practices are paramount. Xobee Networks provides comprehensive IT consulting, advanced cloud hosting solutions, robust backup redundancies, and data restoration services. Our cybersecurity offerings, including virus protection and spam filtering, help safeguard your business from emerging threats. Trust Xobee Networks to keep your technology secure and efficient.
For more information on how to protect you and your business, contact one of our highly skilled technicians today.
Xobee Networks now has engineers servicing clients within Fresno, Clovis, Madera, San Jose, Sacramento, San Francisco & the Bay Area, Los Angeles, Santa Monica, Las Vegas, Bakersfield, San Diego, San Luis Obispo, Anaheim, Palm Springs, and more.
Cody Sarhan | Communications Specialist, Xobee Networks